Approve Microsoft 365 app access
Overview
For some companies, access to Office 365 / Outlook resources is restricted. If you can’t login from Jira yourself, your Office 365 administrator might need to consent to the app for you.
In case you are interested in the exact permissions and why we need them, please check out this dedicated permissions article.
Approving access for all users
To approve access for the app for all users, please send your Office 365 administrator the following link.
--- Short URL
https://go.yasoon.com/outlook-meetings-admin-consent
--- Or use the direct URL
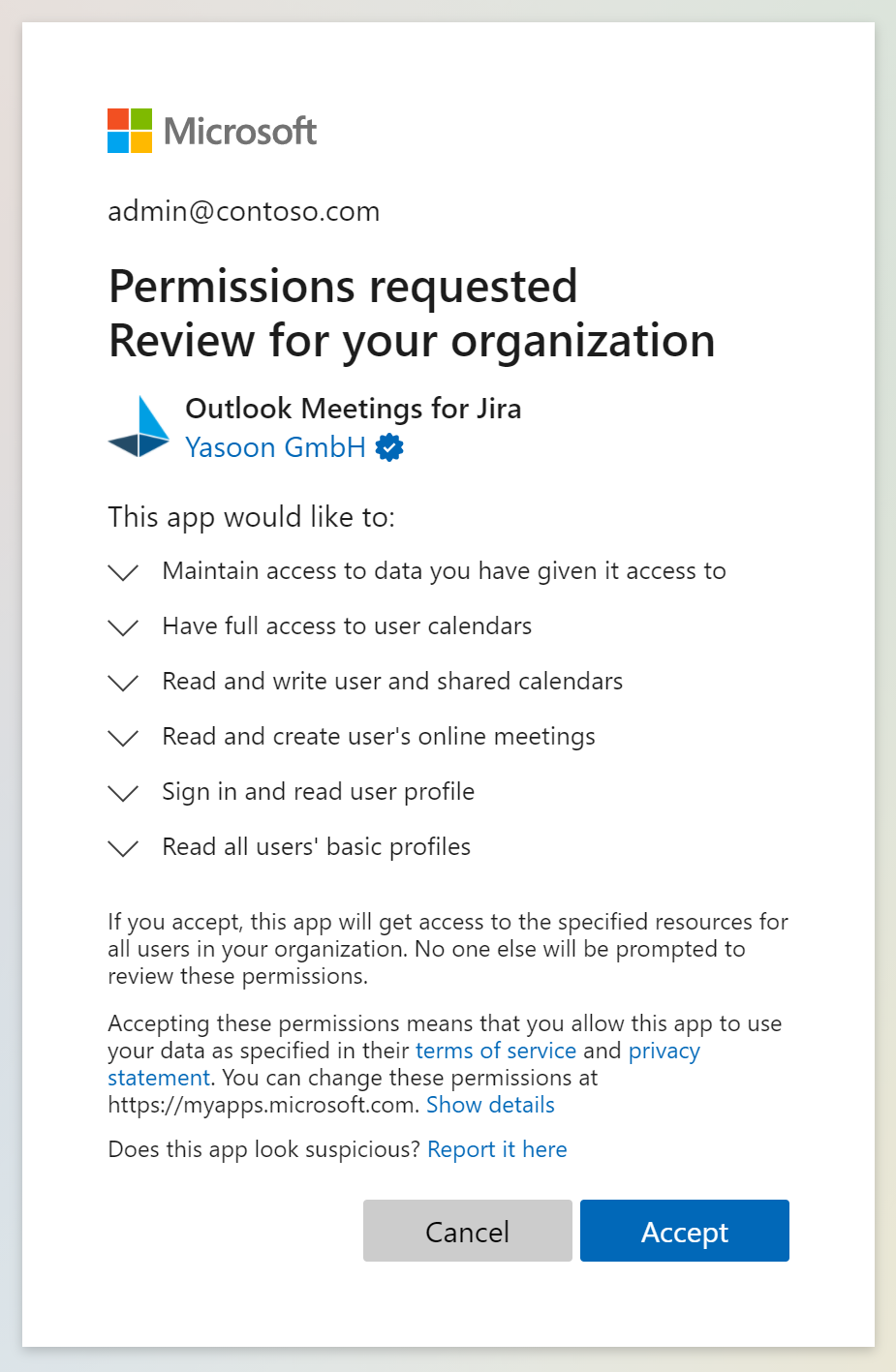
https://login.microsoftonline.com/organizations/v2.0/adminconsent?client_id=fb930189-fe2c-4b11-b424-f576f7b371b3&state=no&redirect_uri=https%3a%2f%2fatlassianconnect.yasoon.com%2fviews%2flogin-success.html&scope=https%3a%2f%2fgraph.microsoft.com%2f.defaultYour admin will see the following screen, where the permissions can be confirmed. Please note, that despite what the screen says in the subtext, we won’t get access to all user resources after approving this. Before we can get access to any Outlook calendar data, the users will need to log in with their own account as well from Jira.
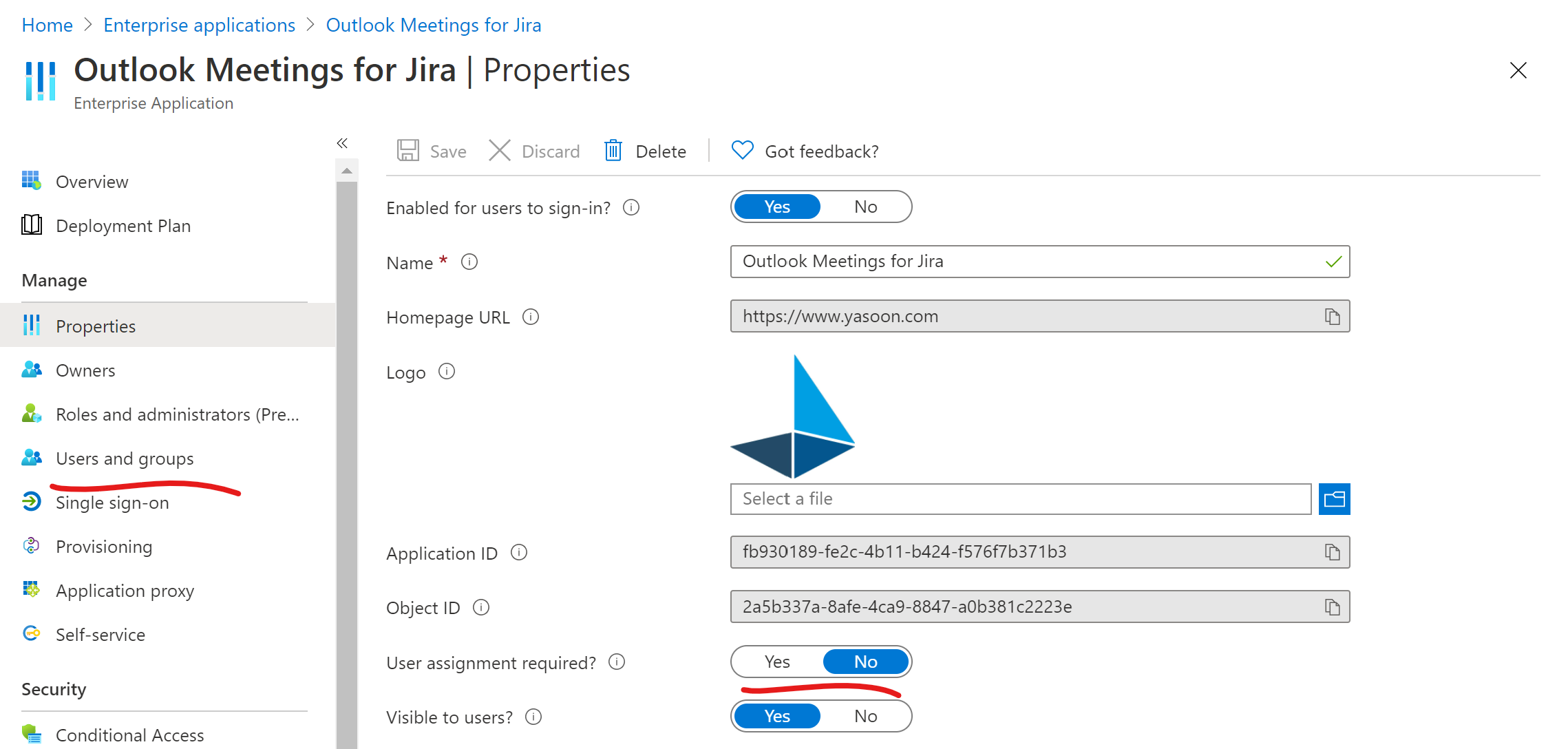
Approving access for a limited set of users
In case you only want to approve the access for a limited set of users, e.g. you already have a dedicated AzureAD group for Jira users, please follow the steps below.
Usually, when approving the app for the first time, it’ll create a “service principal / enterprise application” in your AzureAD tenant. You can check if you already have an enterprise app by checking this page (search for “Outlook Meetings” or “Jira”):
https://portal.azure.com/#blade/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/AllApps/menuId/
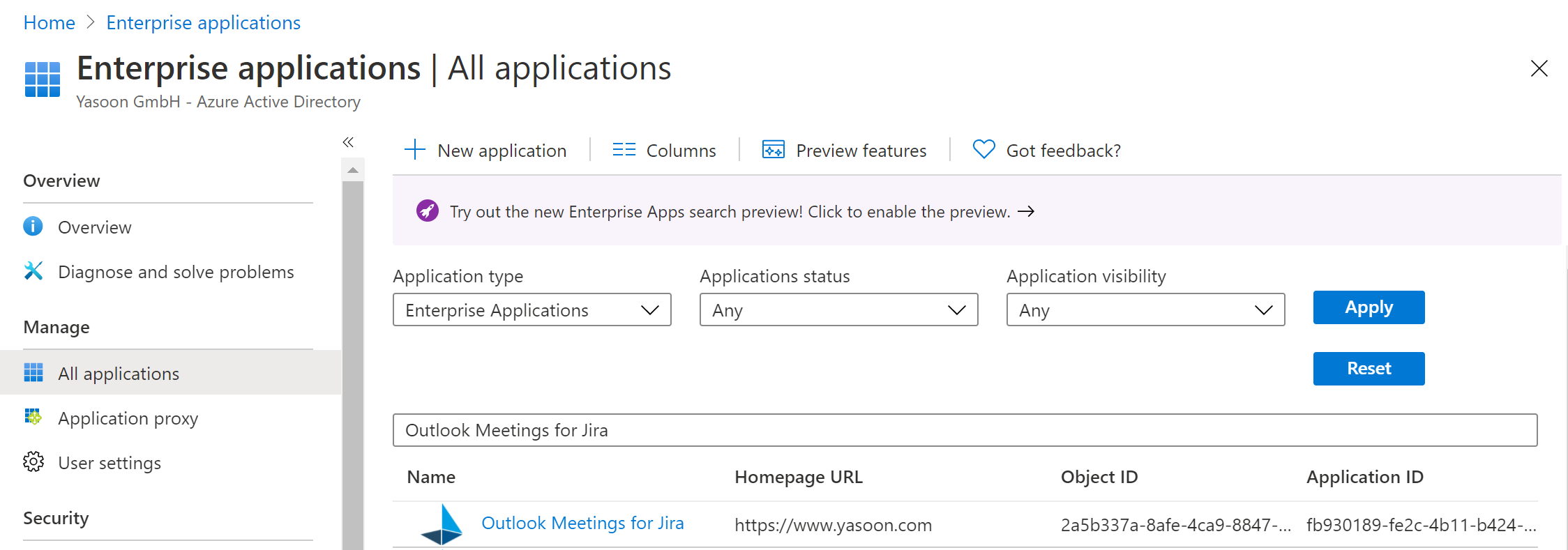
If you don’t have an entry for our app yet, you’ll need to use Powershell to create it manually.
# Install Powershell module for Azure (if you don't have it yet)
Install-Module AzureAD
# Connect to Azure interactively
Connect-AzureAD -Confirm
# Create the new service principal
New-AzureADServicePrincipal -AppId fb930189-fe2c-4b11-b424-f576f7b371b3 -Tags {WindowsAzureActiveDirectoryIntegratedApp}Afterwards, you should be able to find the enterprise app in the UI linked above, where you can restrict the application to certain users or groups, or allow all users to self-approve the app: